
The SOC methodology
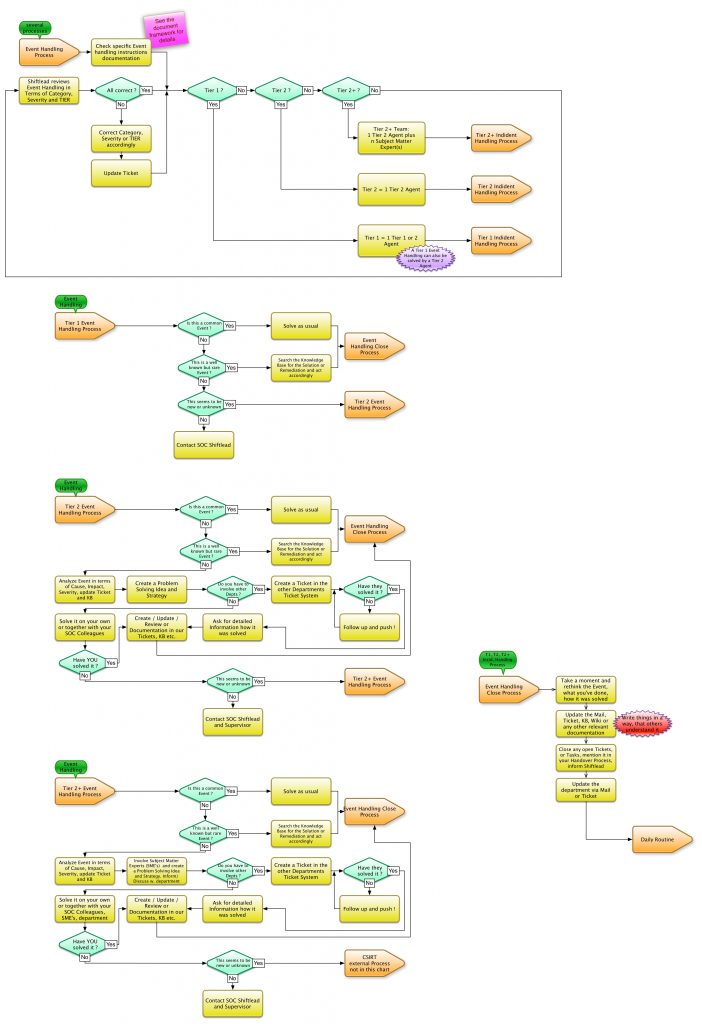
First, let the extract of an SOC workflow (next graphic) takes effect on you (the shift transfer, the daily routine tasks and the end of the shift are missing for a better overview). Please remember, the SOC handles the fast processing of events. If these are known – or easy to solve – this is forwarded from the SOC to the relevant division (IT-Security, Networking, Servers etc.). If events are not easy to solve or completely unknown, they will be forwarded to the CSIRT.
Furthermore, the SOC does not make any changes to IT security assets or the IT infrastructure itself, which is the responsibility of the relevant division. These are informed by tickets. The SOC also takes care that tickets are worked on and closed in a timely manner. If not the SOC agents will escalate to their supervisor.
The workflow briefly explained
The above workflow shows how to handle an event, where plausibility checks are made, when to contact the SOC supervisor, and when to do the necessary documentation, escalation, or hand-off to another department or division. The SOC with this Workflow has a 3 tier structure named Tier 1, Tier 2, and Tier 2+, the employees are the agents.
Tier 1: Here are typically the “new ones” who solve events by means of “learning by doing” and with the help of knowledgebase and their colleagues.
Tier 2: Experienced employees who can handle most events from experience, know the workflows and other procedures well, and to an extent analyze events to a certain depth. These train the Tier 1 agents in daily business.
Tier 2+: I have chosen this name deliberately, because this escalation level or complexity of an event requires SME’s (Subject Matter Expert) support. This can be one or more, even rotating in the processing. Just imagine, a Chinese website is constantly scanning. Then you want to know for sure what information is on the website. Since you can not speak Chinese, ask the Chinese logistics representative next door if he can translate it. Then the Chinese employee becomes the SME for the translation.
If the event can not be solved even in Tier 2+, it will be handed over to the CSIRT by Ticket.
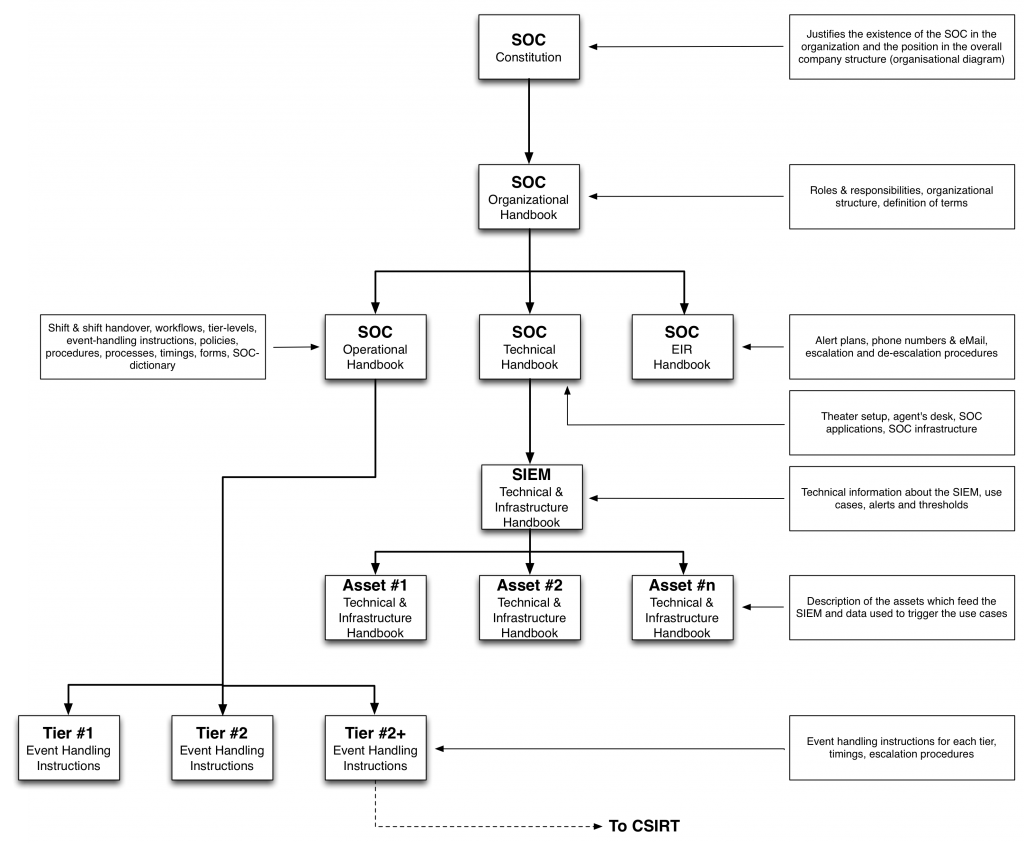
Is actually pretty easy. All procedures, escalations, organization, etc. are again in the document framework, this time for the SOC.
The needed document framework
I have proved that this methodology, document frameworks and workflows work in various SOCs in the field of MSSP, oil mining, finance and telecommunications as a project manager and trainer. What it definitely requires is discipline in terms of tickets, feeding knowledge into the knowledge base, watching tickets for escalation and write tickets in a manner that others can fully understand what have been done.
In addition to these organizational tasks, an SOC must be ergonomically correct, i.e. the right information at the right time on the right screens, the ergonomics of the desk with multiple screens and not forgetting the physical security, i.e. Access locks, securing the SOC space and its infrastructure. But these are initial problems that can be solved relatively easily, assuming proper planning.
Unfortunately – and especially the SOC’s – these IT security organizations suffer from the problem of information overload, noise and false positives, so I always had to optimize the SIEM as part of building SOC and CSIRT.
I will explain in another blog article why 99% of all SIEM’s are not working properly and consuming too much budget.

Recent Comments